Article version: Enterprise Server 2.17
Configuring the default visibility of new repositories on your appliance
You can set the default visibility for all new repositories created via the web interface on your GitHub Enterprise Server appliance to be private or public.
Each time someone creates a new repository on your GitHub Enterprise Server instance, that person must choose a visibility for the repository. When you configure a default visibility setting for the instance, you choose which visibility is selected by default. For more information on repository visibility, see "About repository visibility."
If a site administrator disallows members from creating certain types of repositories, members will not be able to create that type of repository even if the visibility setting defaults to that type. For more information, see "Restricting repository creation in your instance."
Tip: You can restrict the ability to change repository visibility to site administrators only. For more information, see "Preventing users from changing a repository's visibility."
- In the upper-right corner of any page, click .
- In the left sidebar, click Enterprise.
- In the enterprise account sidebar, click Settings.
- Under " Settings", click Options.
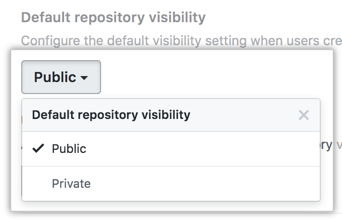
- Under "Default repository visibility", use the drop-down menu and select a default visibility.
Warning: If you add an image attachment to a pull request or issue comment, anyone can view the anonymized image URL without authentication, even if the pull request is in a private repository, or if private mode is enabled. To keep sensitive images private, serve them from a private network or server that requires authentication.