Using LDAP
LDAP lets you authenticate GitHub Enterprise Server against your existing accounts and centrally manage repository access. LDAP is a popular application protocol for accessing and maintaining directory information services, and is one of the most common protocols used to integrate third-party software with large company user directories.
If you want to authenticate users without adding them to your identity provider, you can configure built-in authentication. For more information, see "Allowing built-in authentication for users outside your identity provider."
In this guide:
- Supported LDAP services
- Username considerations with LDAP
- Two-factor authentication
- Configuring LDAP with your GitHub Enterprise Server instance
- LDAP attributes
- Viewing and creating LDAP users
- Updating LDAP accounts
- Revoking access to your GitHub Enterprise Server instance
Supported LDAP services
GitHub Enterprise Server integrates with these LDAP services:
- Active Directory
- FreeIPA
- Oracle Directory Server Enterprise Edition
- OpenLDAP
- Open Directory
- 389-ds
Username considerations with LDAP
GitHub Enterprise Server usernames can only contain alphanumeric characters and dashes (-). GitHub Enterprise Server will normalize any non-alphanumeric character in your account's username into a dash. For example, a username of gregory.st.john will be normalized to gregory-st-john. Note that normalized usernames also can't start or end with a dash. They also can't contain two consecutive dashes.
Usernames created from email addresses are created from the normalized characters that precede the @ character.
If multiple accounts are normalized into the same GitHub Enterprise Server username, only the first user account is created. Subsequent users with the same username won't be able to sign in.
This table gives examples of how usernames are normalized in GitHub Enterprise Server:
| Username | Normalized username | Result |
|---|---|---|
| Ms.Bubbles | ms-bubbles |
This username is created successfully. |
| !Ms.Bubbles | -ms-bubbles |
This username is not created, because it starts with a dash. |
| Ms.Bubbles! | ms-bubbles- |
This username is not created, because it ends with a dash. |
| Ms!!Bubbles | ms--bubbles |
This username is not created, because it contains two consecutive dashes. |
| Ms!Bubbles | ms-bubbles |
This username is not created. Although the normalized username is valid, it already exists. |
| Ms.Bubbles@example.com | ms-bubbles |
This username is not created. Although the normalized username is valid, it already exists. |
Two-factor authentication
When using LDAP or built-in authentication, two-factor authentication is supported. Organization administrators can require members to have two-factor authentication enabled.
Configuring LDAP with your GitHub Enterprise Server instance
After you configure LDAP, users will be able to sign into your instance with their LDAP credentials. When users sign in for the first time, their profile names, email addresses, and SSH keys will be set with the LDAP attributes from your directory.
When you configure LDAP access for users via the Management Console, your seats aren't used until the first time a user signs in to your instance. However, if you create an account manually using site admin settings, the seat is immediately accounted for.
Warning: Before configuring LDAP on your GitHub Enterprise Server instance, make sure that your LDAP service supports paged results.
-
In the upper-right corner of any page, click .

-
In the left sidebar, click Management Console.
-
In the left sidebar, click Authentication.
-
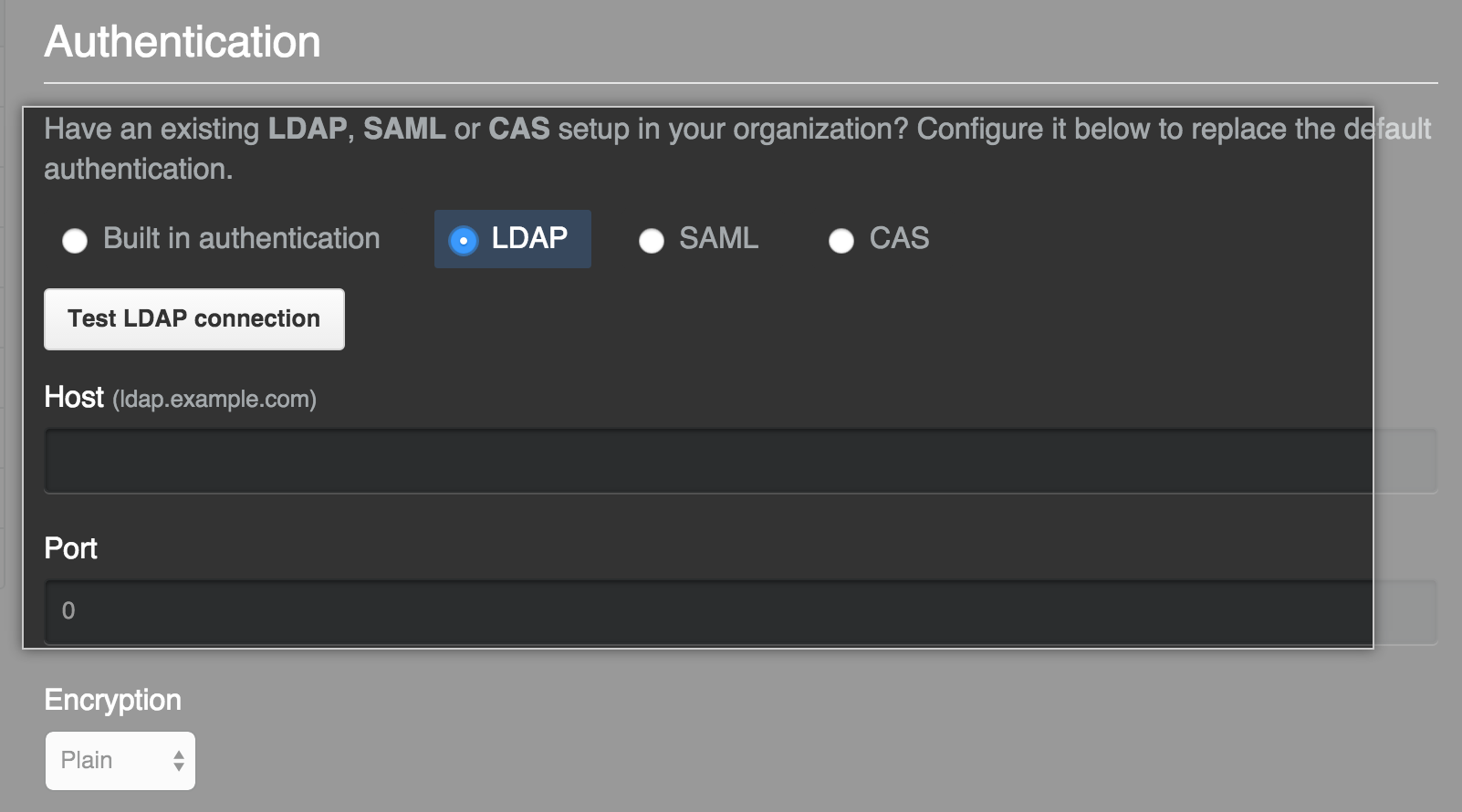
Under "Authentication", select LDAP.
-
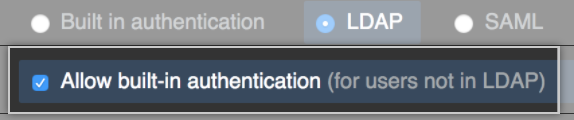
Optionally, select Allow built-in authentication to invite users to use built-in authentication if they don’t belong to your GitHub Enterprise Server instance's identity provider.
-
Add your configuration settings.
LDAP attributes
Use these attributes to finish configuring LDAP for your GitHub Enterprise Server instance.
| Attribute name | Type | Description |
|---|---|---|
Host |
Required | The LDAP host, e.g. ldap.example.com or 10.0.0.30. If the hostname is only available from your internal network, you may need to configure your GitHub Enterprise Server instance's DNS first so it can resolve the hostname using your internal nameservers. |
Port |
Required | The port the host's LDAP services are listening on. Examples include: 389 and 636 (for LDAPS). |
Encryption |
Required | The encryption method used to secure communications to the LDAP server. Examples include plain (no encryption), SSL/LDAPS (encrypted from the start), and StartTLS (upgrade to encrypted communication once connected). |
Domain search user |
Optional | The LDAP user that performs user lookups to authenticate other users when they sign in. This is typically a service account created specifically for third-party integrations. Use a fully qualified name, such as cn=Administrator,cn=Users,dc=Example,dc=com. With Active Directory, you can also use the [DOMAIN]\[USERNAME] syntax (e.g. WINDOWS\Administrator) for the domain search user with Active Directory. |
Domain search password |
Optional | The password for the domain search user. |
Administrators group |
Optional | Users in this group are promoted to site administrators when signing into your appliance. If you don't configure an LDAP Administrators group, the first LDAP user account that signs into your appliance will be automatically promoted to a site administrator. |
Domain base |
Required | The fully qualified Distinguished Name (DN) of an LDAP subtree you want to search for users and groups. You can add as many as you like; however, each group must be defined in the same domain base as the users that belong to it. If you specify restricted user groups, only users that belong to those groups will be in scope. We recommend that you specify the top level of your LDAP directory tree as your domain base and use restricted user groups to control access. |
Restricted user groups |
Optional | If specified, only users in these groups will be allowed to log in. You only need to specify the common names (CNs) of the groups, and you can add as many groups as you like. If no groups are specified, all users within the scope of the specified domain base will be able to sign in to your GitHub Enterprise Server instance. |
User ID |
Required | The LDAP attribute that identifies the LDAP user who attempts authentication. Once a mapping is established, users may change their GitHub Enterprise Server usernames. This field should be sAMAccountName for most Active Directory installations, but it may be uid for other LDAP solutions, such as OpenLDAP. The default value is uid. |
Profile name |
Optional | The name that will appear on the user's GitHub Enterprise Server profile page. Unless LDAP Sync is enabled, users may change their profile names. |
Emails |
Optional | The email addresses for a user's GitHub Enterprise Server account. |
SSH keys |
Optional | The public SSH keys attached to a user's GitHub Enterprise Server account. The keys must be in OpenSSH format. |
GPG keys |
Optional | The GPG keys attached to a user's GitHub Enterprise Server account. |
Disable LDAP authentication for Git operations |
Optional | If selected, turns off users' ability to use LDAP passwords to authenticate Git operations. |
Enable LDAP certificate verification |
Optional | If selected, turns on LDAP certificate verification. |
Synchronization |
Optional | If selected, turns on LDAP Sync. |
Disabling password authentication for Git operations
Select Disable username and password authentication for Git operations in your LDAP settings to enforce use of personal access tokens or SSH keys for Git access, which can help prevent your server from being overloaded by LDAP authentication requests. We recommend this setting because a slow-responding LDAP server, especially combined with a large number of requests due to polling, is a frequent source of performance issues and outages.
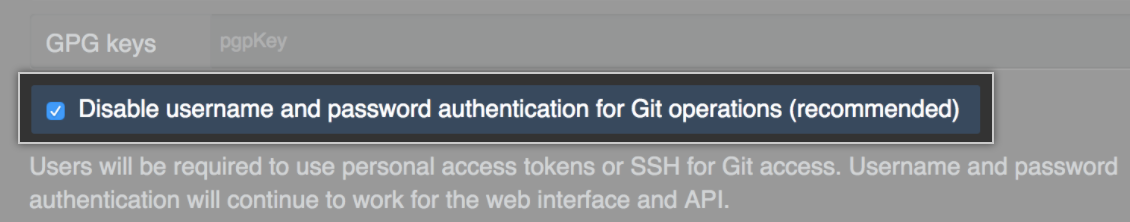
When this option is selected, if a user tries to use a password for Git operations via the command line, they will receive an error message that says, Password authentication is not allowed for Git operations. You must use a personal access token.
Enabling LDAP certificate verification
Select Enable LDAP certificate verification in your LDAP settings to validate the LDAP server certificate you use with TLS.
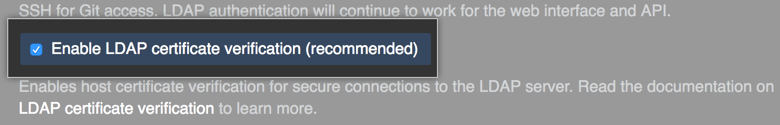
When this option is selected, the certificate is validated to make sure:
- If the certificate contains at least one Subject Alternative Name (SAN), one of the SANs matches the LDAP hostname. Otherwise, the Common Name (CN) matches the LDAP hostname.
- The certificate is not expired.
- The certificate is signed by a trusted certificate authority (CA).
Enabling LDAP Sync
LDAP Sync lets you synchronize GitHub Enterprise Server users and team membership against your established LDAP groups. This lets you establish role-based access control for users from your LDAP server instead of manually within GitHub Enterprise Server. For more information, see "Creating teams."
To enable LDAP Sync, in your LDAP settings, select Synchronize Emails, Synchronize SSH Keys, or Synchronize GPG Keys .
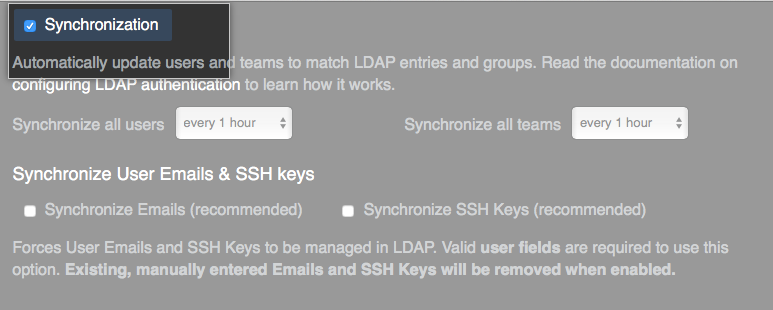
After you enable LDAP sync, a synchronization job will run at the specified time interval to perform the following operations on each user account:
- If you've allowed built-in authentication for users outside your identity provider, and the user is using built-in authentication, move on to the next user.
- If no LDAP mapping exists for the user, try to map the user to an LDAP entry in the directory. If the user cannot be mapped to an LDAP entry, suspend the user and move on to the next user.
- If there is an LDAP mapping and the corresponding LDAP entry in the directory is missing, suspend the user and move on to the next user.
- If the corresponding LDAP entry has been marked as disabled and the user is not already suspended, suspend the user and move on to the next user.
- If the corresponding LDAP entry is not marked as disabled, and the user is suspended, and Reactivate suspended users is enabled in the Admin Center, unsuspend the user.
- If the corresponding LDAP entry includes a
nameattribute, update the user's profile name. - If the corresponding LDAP entry is in the Administrators group, promote the user to site administrator.
- If the corresponding LDAP entry is not in the Administrators group, demote the user to a normal account.
- If an LDAP User field is defined for emails, synchronize the user's email settings with the LDAP entry. Set the first LDAP
mailentry as the primary email. - If an LDAP User field is defined for SSH public keys, synchronize the user's public SSH keys with the LDAP entry.
- If an LDAP User field is defined for GPG keys, synchronize the user's GPG keys with the LDAP entry.
Note: LDAP entries can only be marked as disabled if you use Active Directory and the userAccountControl attribute is present and flagged with ACCOUNTDISABLE.
A synchronization job will also run at the specified time interval to perform the following operations on each team that has been mapped to an LDAP group:
- If a team's corresponding LDAP group has been removed, remove all members from the team.
- If LDAP member entries have been removed from the LDAP group, remove the corresponding users from the team. If the user loses access to any repositories as a result, delete any private forks the user has of those repositories.
- If LDAP member entries have been added to the LDAP group, add the corresponding users to the team. If the user regains access to any repositories as a result, restore any private forks of the repositories that were deleted because the user lost access in the past 90 days.
As part of its optimization configuration, LDAP Sync will not transfer your nested team structure. To create child and parent team relationships, you must manually recreate the nested team structure and sync it with the corresponding LDAP group. For more information, see "Creating teams"
Security Warning:
When LDAP Sync is enabled, site admins and organization owners can search the LDAP directory for groups to map the team to.
This has the potential to disclose sensitive organizational information to contractors or other unprivileged users, including:
- The existence of specific LDAP Groups visible to the Domain search user.
- Members of the LDAP group who have GitHub Enterprise Server user accounts, which is disclosed when creating a team synced with that LDAP group.
If disclosing such information is not desired, your company or organization should restrict the permissions of the configured Domain search user in the admin console. If such restriction isn't possible, contact GitHub Enterprise Support or GitHub Premium Support.
Supported LDAP group object classes
GitHub Enterprise Server supports these LDAP group object classes. Groups can be nested.
groupgroupOfNamesgroupOfUniqueNamesposixGroup
Viewing and creating LDAP users
You can view the full list of LDAP users who have access to your instance and provision new users.
-
Sign in to your GitHub Enterprise Server instance at
http(s)://HOSTNAME/login. -
In the upper-right corner of any page, click .

-
In the left sidebar, click LDAP users.
-
To search for a user, type a full or partial username and click Search. Existing users will be displayed in search results. If a user doesn’t exist, click Create to provision the new user account.

Updating LDAP accounts
Unless LDAP Sync is enabled, changes to LDAP accounts are not automatically synchronized with GitHub Enterprise Server.
- To use a new LDAP admin group, users must be manually promoted and demoted on GitHub Enterprise Server to reflect changes in LDAP.
- To add or remove LDAP accounts in LDAP admin groups, promote or demote the accounts on GitHub Enterprise Server.
- To remove LDAP accounts, suspend the GitHub Enterprise Server accounts.
Manually syncing LDAP accounts
-
Sign in to your GitHub Enterprise Server instance at
http(s)://HOSTNAME/login. -
In the upper-right corner of any page, click .

-
In the search field, type the name of the user and click Search.
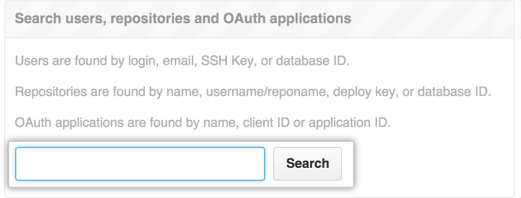
-
In the search results, click the name of the user.
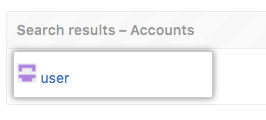
-
In the upper-right corner of the page, click Admin.

-
In the left sidebar, click Admin.
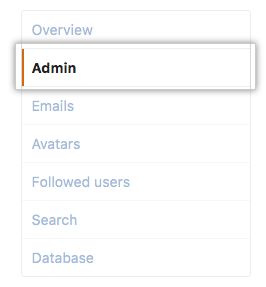
-
Under "LDAP," click Sync now to manually update the account with data from your LDAP server.
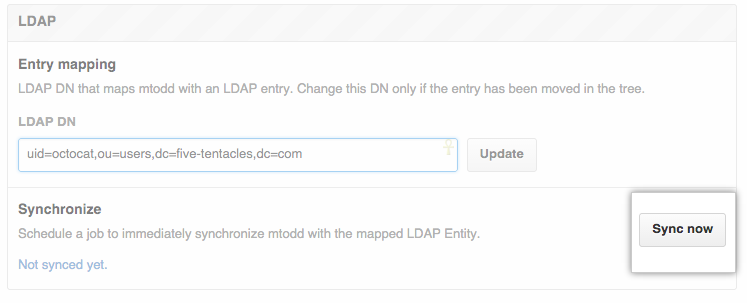
You can also use the API to trigger a manual sync.
Revoking access to your GitHub Enterprise Server instance
If LDAP Sync is enabled, removing a user's LDAP credentials will suspend their account after the next synchronization run.
If LDAP Sync is not enabled, you must manually suspend the GitHub Enterprise Server account after you remove the LDAP credentials. For more information, see "Suspending and unsuspending users".